Advanced Approaches to Network Threat Detection

Key Takeaways
- Network threat detection is essential in securing digital spaces from malicious attacks.
- Integrating AI and machine learning enhances detection and response capabilities.
- Comprehensive visibility across network traffic is crucial for detecting anomalies in real-time.
- Businesses need a layered security approach to counteract sophisticated threats effectively.
Table of Contents
- Introduction to Network Threat Detection
- AI and ML in Threat Detection
- Importance of Comprehensive Network Visibility
- Real-Time Anomaly Detection Techniques
- Benefits of a Layered Security Approach
- Challenges in Implementing Network Threat Detection
- Future Trends in Network Security
- Key Considerations for Businesses
In today’s increasingly digital world, securing your network against potential threats has become more essential than at any other time in history. Organizations of all sizes and across industries find themselves facing the relentless challenge of defending their sensitive data and critical resources from a myriad of cyber threats. The digital battleground is fraught with challenges presented by bad actors constantly seeking to exploit system vulnerabilities for malicious gain. Thus, one might wonder how businesses effectively anticipate and mitigate these ever-evolving cyber threats. The answer lies in comprehensive network detection and response solutions. These intricate systems offer advanced protection by meticulously analyzing patterns and detecting anomalies within network traffic, enabling timely intervention to address potential vulnerabilities before they can be exploited.
From thwarting hackers who attempt data breaches to averting malware infiltrations, the digital landscape is replete with threats that can profoundly disrupt business operations and compromise sensitive information. Consequently, effective network threat detection systems are not optional but an existential necessity for contemporary organizations. These systems must be dynamic and agile, capable of handling a broad spectrum of threats while providing invaluable threat intelligence to inform strategic decision-making and bolster organizational resilience.
Introduction to Network Threat Detection
The stakes have never been higher when it comes to network security, as enterprises today are besieged by a multitude of threats ranging from encrypting ransomware and deceptive phishing attacks to elusive zero-day vulnerabilities that have the potential to cripple operations overnight. Such pervasive risks necessitate that network threat detection becomes a cornerstone of modern cybersecurity strategies, enabling organizations to preemptively identify and thwart threats before these adversaries can inflict significant damage. Without robust mechanisms in place, the consequences can extend far beyond financial loss to erosion of reputation and customer trust—intangibles that can be far more challenging to restore once undermined.
AI and ML in Threat Detection
AI and ML have truly revolutionized the way threats are detected and managed in the dynamic fields of cybersecurity. These cutting-edge technologies offer unprecedented capabilities by allowing systems to learn from past incidents, foresee potential threats, and respond proactively with remarkable speed and accuracy. By leveraging extensive datasets, AI can discern intricate patterns that might otherwise escape human analysts. This capability is crucial in identifying vulnerabilities and issuing alerts for anomalies that may signal potential issues. For an industry where every minute counts, such capabilities are essential, significantly reducing the time from threat detection to response and enabling organizations to stay a significant step ahead in their cybersecurity race.
Importance of Comprehensive Network Visibility
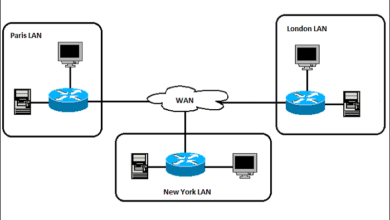
Maintaining clear and unobstructed visibility across all network traffic is not merely beneficial but a critical necessity in today’s hyper-connected digital environment. Comprehensive network visibility empowers security teams to monitor activities vigilantly, identifying unusual patterns or deviations that could signify potential threats. By utilizing advanced monitoring tools, organizations enhance this visibility, thus enabling them to detect and respond to malicious activities that might otherwise evade detection. Establishing an infrastructure that supports continuous surveillance and detailed analytics becomes foundational to effective threat detection. It empowers organizations to act decisively and swiftly when threats materialize, ensuring business operations remain uninterrupted and secure.
Real-Time Anomaly Detection Techniques
Real-time anomaly detection technologies employ a diverse array of strategies to maintain network security, vigilantly analyzing data patterns to detect any deviations from established norms. Techniques such as statistical anomaly detection provide robust frameworks for early identification of suspicious activities, signaling potential security breaches and enabling organizations to intervene proactively. These strategic techniques boost situational awareness, ensuring that systems remain alert to novel threats and allowing organizations to fortify their defenses and uphold a robust posture against cyber adversaries, preserving the integrity and confidentiality of their digital assets.
Benefits of a Layered Security Approach
Adopting a layered security strategy is paramount in today’s complex and multi-faceted threat landscape. By deploying an amalgamation of security measures—ranging from intrusion prevention systems and robust firewalls to endpoint protections and encryption protocols—organizations establish a multi-faceted defense that exponentially complicates any cyber incursions. This strategic approach ensures that even if one defensive measure fails, other layers remain to protect the organization’s assets. Such comprehensive approaches underscore the principle that no single threat should find an easy entry, effectively mitigating risks and safeguarding sensitive data from unauthorized access and theft.
Challenges in Implementing Network Threat Detection
Despite the evident benefits, the implementation of network threat detection systems is not without its challenges. Organizations must wisely calibrate detection sensitivity to balance effectiveness against overload, as excessive false positives can lead to alert fatigue amongst security teams and unnecessarily strain resources. Furthermore, integrating such sophisticated systems into existing IT infrastructure demands careful planning and can often be resource-intensive—requiring specialized skillsets and knowledge to ensure seamless functionality.
Future Trends in Network Security
The future of network security is approaching a transformational zenith as technology continues to evolve at an unprecedented pace. Emerging trends are redefining how networks are protected. While these technologies bring significant opportunities, they also introduce new challenges by increasing the potential entry points for cyber threats, thereby necessitating even more sophisticated and adaptive threat detection systems. As organizations embrace these technological advancements, a proactive and forward-thinking approach to network security will be essential for long-term success and resilience.
Key Considerations for Businesses
Businesses aspiring to enhance their network security must remain agile and adaptable to the perpetually evolving threat landscape. Striking an effective balance between cost-efficiency and robust protection is critical when implementing comprehensive network security strategies. Continuous adaptation and regular security assessments are vital components in maintaining robust defenses, ensuring that businesses stay abreast of both internal vulnerabilities and emerging external threats. By consulting resources illustrating the contributions of AI and machine learning to modern security strategies, companies can refine their strategies to enhance detection capabilities.