Essential DevSecOps Best Practices for Secure Software Development
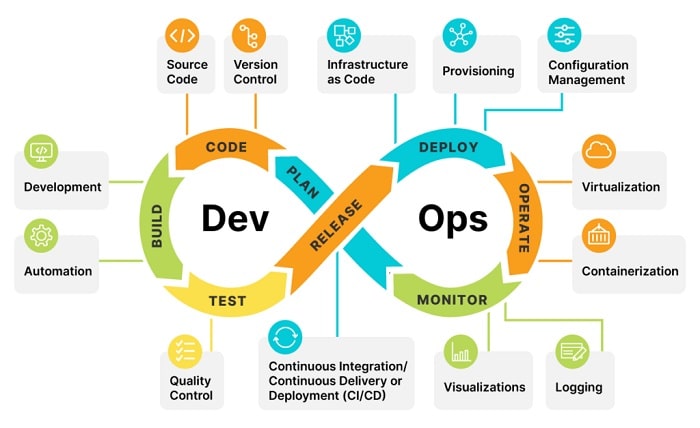
DevSecOps is the extension of security to DevOps; this involves cycling security within the development structure, thus seeking and fixing security flaws at an early stage. DevSecOps Best Practices is different from traditional practices in the sense that it integrates security into the early, middle, and end of the development life cycle. These gestures contribute to ensuring the quality and security of the software since security issues are not only considered at the end of the process.
Benefits of DevSecOps
In modern society, security threats are dynamic, hence warranting the application of DevSecOps to ensure the safety of the development processes. When security is considered in the early stages of the project, quality is already the key factor that a team labors hard to achieve, not necessarily because it is the last thing that needs to be implemented. The given approach contributes to a shorter time for issues, lower security expenses, optimized processes, improved compliance, and fewer exposures.
Key DevSecOps Best Practices
Start slow and plan strategically.
DevSecOps requires the engagement of many players; therefore, some changes are not easy to introduce. First of all, identify a strategy to be implemented clearly and realistically while meeting the objectives of the development, operation, testing, and security teams. Both teams have to work to detect vulnerable security situations efficiently.
Teach the Principles of Team Members
Security in the contemporary working environment should not be the preserve of a few people who are on the special security team of an organization. Informing the team regarding this joint approach also fosters the implementation of the DevSecOps approach concerning habits. Appointing security champions for teams can extend the security focus to the specific team and relate to major decisions taken within that team.
Build the right teams.
It is crucial to continuously form detailed groups as a line of defense. The reds are the ethical hackers who can mimic such an occasion, while the blue parties are the ones who have to address this event. Also, the introduction of a bug bounty program that recognizes the team members who find the gaps encourages a team to be more security-conscious.
Foster a security culture.
Ensuring security is one of the practices that should be taken seriously when implementing DevSecOps. Promote security in the organization at the people level, process level, and technological level. Youth support also means that security goals and objectives should be set by the top management. Having well-defined channels and SLAs means that teams focus on security because response and resolution are well-defined.
Emphasize continuous practice.
DevSecOps is a continual process, and hence feedback is required regularly. Every project has a fresh opportunity, letting the teams innovate and enhance their practice step by step. Addressing malfunctions and delays reduces the risks to the security solutions as the teams become more familiar with them.
Manage incidents effectively.
Security is the core design principle, and having a dedicated incident management plan is mandatory. Terms such as the workflow, the responsibility, and the action plan ensure that challenges presented are solved systematically and effectively by the teams present.
Promoting simple yet secure coding habits
Incorporation of security standards in coding enhances the development process because strong code is easy to write. Procedures for code verification and testing are well defined, thereby enabling developers and testers to create secure code substances.
Develop guidelines on how coding and change management will be done internally.
In addition to following best coding practices, the creation of internal standards and the formation of training programs are two more kinds of insurance. Daily scans and easy-to-develop security concepts ensure protected environments for development.
Conduct regular audits.
An internal and external audit is vital for learning about the organization’s exposure to risk and the preparedness of the implemented system. The implementation of security plans can be monitored with the help of annual audits to find out ways to correct something.
Test Vigorously
Testing is conducted in all phases of software development so that problems can be identified early in their development. Speed and thoroughness are crucial considerations as well: live testing, analysis of input parameters, and fine-tuning of processes. It will also be noted that automation testing tools are efficient in assessing and testing third-party dependencies and open-source applications.
Utilize automation and tools.
Instead, automation remains a way of meeting the required deadlines in a manner that does not endanger the security of the networks. The testing for code and application involves static application security testing (SAST) and dynamic application security testing (DAST). The optimization of the alerts and utilization of considerable reports enhance issue identification and management during the process. Training teams in the use of these tools also promote the proficiency of the tools and teams as well.
Embrace continuous feedback.
Feedback is continuous in the DevSecOps framework. It means that each member of the team is informed about the security situation of the project at that certain point in time. Continuous feedback between development, operation, and security contributes to the fast identification and rectification of security vulnerabilities, resulting in better protection applications.
Read More: istudyinfo a revolutionary way to educate
The Future of DevSecOps
Since security is a crucial parameter in modern software development, security has to be shifted left or moved in the early hours of the SDLC. It is much easier and does not cost as much to resolve issues in this fashion as it does to institute individual lawsuits that have inconsistent results at best. Future trends in DevSecOps will be more rigid time constraints, integration of resources into the cloud environments for developmental and operational purposes, and use of CI frameworks for the integration of security checklists. Firms shall also set out the Key Performance Indicator (KPI) as the benchmark to gauge, monitor, and enhance company security.
Read More: How to Join a Blooket Game: Blooket Join
Conclusion
DevSecOps is valuable as it entails the incorporation of security from the development process to the release. Continuous training, proper planning methods, the formation of specialized teams, and vulnerability testing can all be used to improve the security of an organization. Over the years, the field is bound to develop and reach a point where adopting DevSecOps will be the way to go in ensuring that the processes of development are both secure and efficient.
Read More:
Powering student-centric education in universities & colleges
We help universities and colleges of all sizes and streams run better – from admissions to academics, back office to accreditations, desktop to mobiles – We empower students, faculty and management to collaborate efficiently and use insights effectively, benchmarking quality education while creating personalized learning experience gu icloud
A market leader in end-to-end unified education management solutions




